Authentification & SSO
The Authentication & SSO section enables administrators to define how users log in to the platform, manage single sign-on configurations, and enforce password security policies.
This authentication system works in conjunction with role management to provide secure access to web interfaces and process workflows.
To access it: Go to Account > Settings > Auth from the top navigation menu.
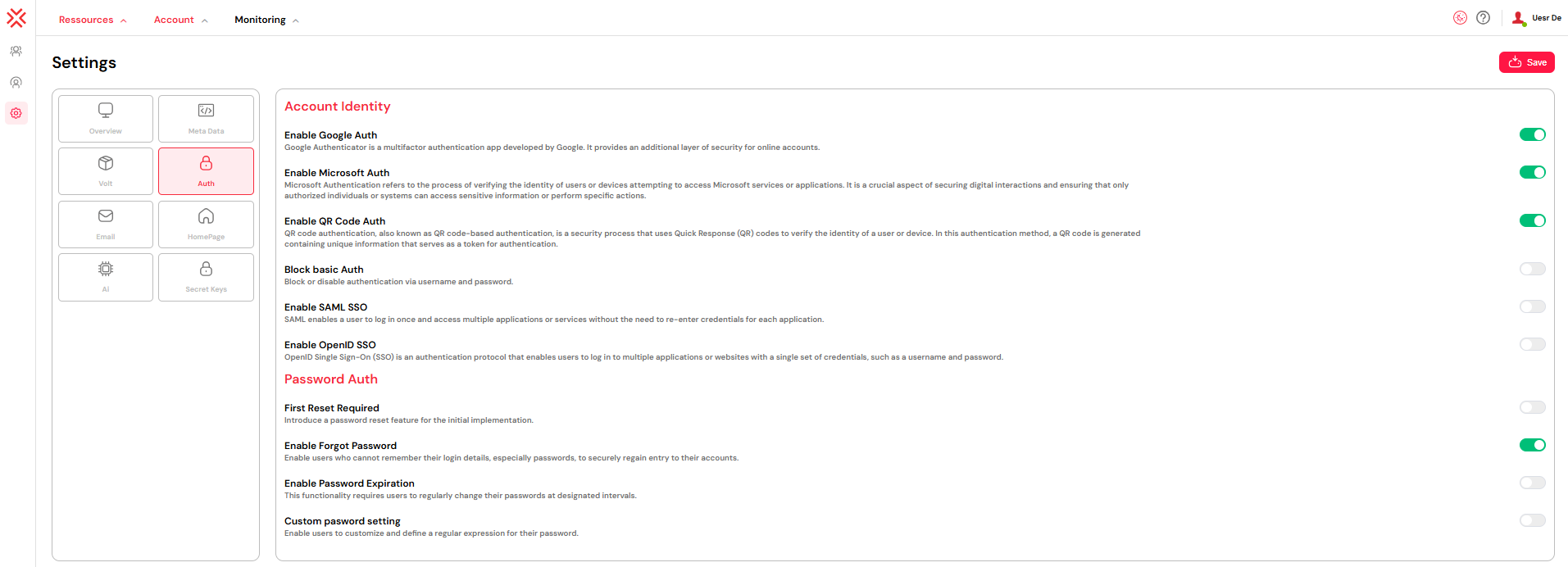
1. Different Authentication methods
Softyflow supports a variety of authentication strategies to meet your security needs:
Google Authenticator (2FA)
Adds a second layer of authentication using time-based one-time codes generated by the Google Authenticator mobile app. After entering their password, users must enter a code from the app to access the platform.
This is particularly important for users with IDE access who can modify applications and processes.

Microsoft Authenticator (2FA)
Functions similarly to Google Authenticator, providing one-time codes via the Microsoft Authenticator mobile app. This enhances protection against password theft and is ideal for organizations using Microsoft ecosystem tools.

QR Code Auth
Allows users to scan a unique QR code with an authentication app to complete their login. This method is typically used for account linking or seamless access flows and works well with mobile applications.

SSO with SAML
Softyflow supports SAML 2.0-based Single Sign-On (SSO), allowing users to log in through your organization's identity provider. This is essential for enterprise environments and integrates seamlessly with user management and role assignments.

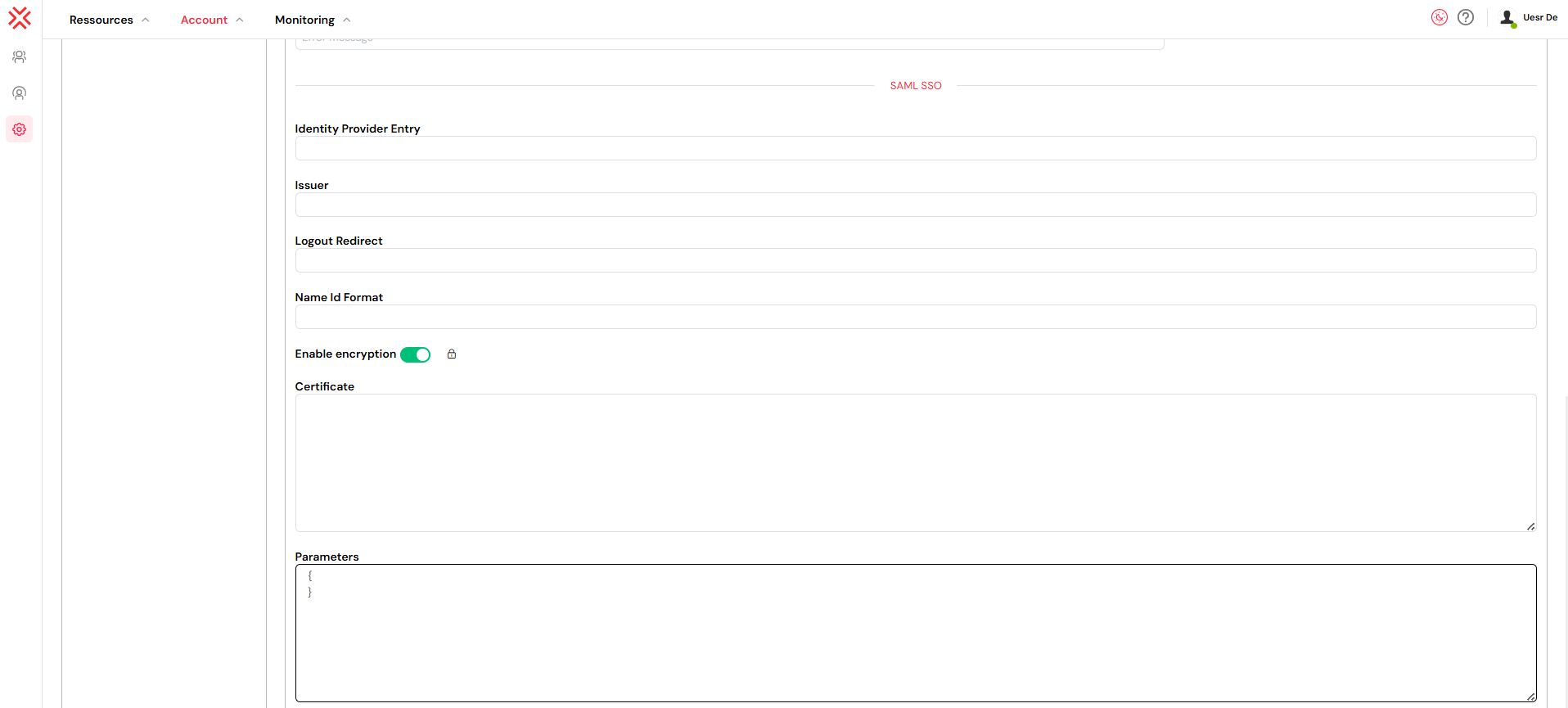
To configure SAML:
Identity Provider Entry: Your company's authentication endpoint.
Issuer: Unique identifier of your SAML configuration.
Logout Redirect: URL where users are redirected post-logout (can be configured with home page redirection).
NameID Format: Defines user identifiers (e.g., email address or persistent ID).
Enable Encryption: Optional setting to encrypt assertions and metadata.
Certificate: Required to verify identity and secure the data exchange.
Parameters: Additional values such as RelayState, ACS URL, and RequestedAuthnContext for advanced configuration.
OpenID Connect (OIDC)
In addition to SAML, Softyflow supports OpenID Connect for modern SSO needs using OAuth 2.0 and JWT-based identity tokens. Ideal for integration with providers like Google, Azure, Okta, and others. This method can be used with API integrations and custom authentication workflows.
2. Password Management
Enforce strong access controls with customizable password policies:
First Login Reset
Force users to reset their password during their first login session. This enhances account protection after admin-initiated user creation.
Enable Forgot Password
Activate this feature to allow users to request a reset link via email if they forget their password. This uses the configured mail providers to send reset links securely.
Password Expiration
Require users to update their password periodically. You can set the number of days before a password expires. This is particularly important for users with elevated privileges or IDE access.
Custom Password Settings
Use regular expressions to enforce password complexity rules (e.g. minimum length, inclusion of numbers/symbols). For example:
Regex: ^(?=.[A-Z])(?=.\d)[A-Za-z\d]{8,}$
Message: "Password must be at least 8 characters, include an uppercase letter and a number."
By combining authentication methods, SSO protocols, and password policies, you can secure access to your platform while adapting to your internal IT practices. These settings work together with role management to ensure users have appropriate access to web interfaces, process workflows, and monitoring tools.
3. Authentication Integration
3.1. Development Considerations
When designing applications, consider authentication requirements:
- Web Interface Design: Design interfaces that adapt to authenticated user context
- Process Design: Create workflows that respect authentication and authorization
- Database Integration: Implement data access controls based on authenticated users
- Integration: Use authentication tokens for external API calls
3.2. Monitoring Authentication
Track authentication activities across your platform:
- System Logs: Monitor login attempts, failed authentications, and security events
- User Management: Review user login history and access patterns
- Run & Instance Management: Track which authenticated users are executing processes
3.3. Security Best Practices
Implement comprehensive security measures:
- Multi-Factor Authentication: Enable 2FA for all users with administrative privileges
- Role-Based Access: Combine authentication with role management for granular control
- Regular Audits: Use system logs to monitor authentication patterns
- Environment Separation: Configure different authentication requirements for test and production environments
4. Next Steps
Continue securing your platform:
Security Administration:
- User Management - Create and manage user accounts with proper authentication
- Role Management - Define access levels that work with authentication
- Settings - Configure platform settings and security policies
- Mail Management - Set up email providers for password reset and notifications
- System Logs - Monitor authentication and security events
- Home Redirection - Create personalized landing pages for authenticated users
Development Security:
- Project Setup - Start building secure applications
- Web Interface Design - Design interfaces with authentication in mind
- Process Design - Create secure workflows with proper authorization
- Integration - Implement secure API integrations and authentication flows