Logs
Logs
The Logs section provides administrators with comprehensive visibility into platform activity and user actions, serving as an audit trail for security, debugging, and compliance purposes.
This logging system integrates with user management, role management, authentication systems, and process monitoring to provide complete platform oversight.
Overview
The logs interface displays all platform activities in a structured table format, allowing administrators to track user behavior, system events, and operational changes across the platform.
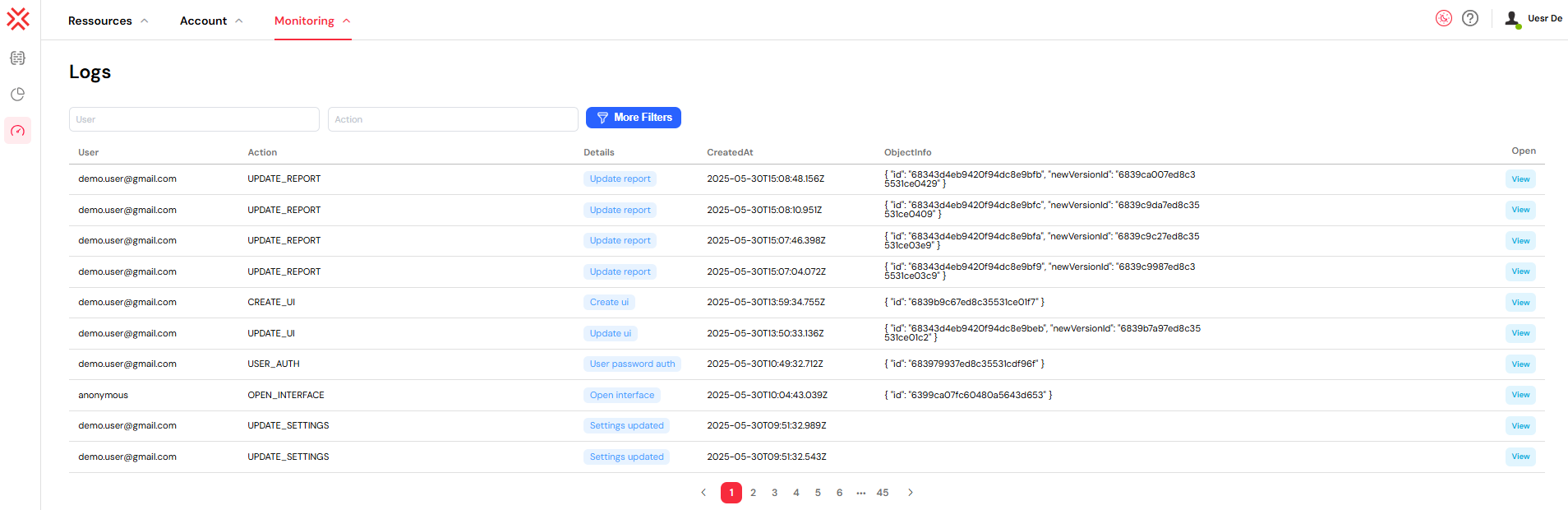
Log Entry Structure
Each log entry contains the following information:
- User: Email address of the user who performed the action
- Action: Type of operation executed (e.g.,
USER_AUTH,ADD_USERS_TO_GROUP,UPDATE_INSTANCE) - Details: Brief description or category of the action
- CreatedAt: Timestamp when the action was executed
- ObjectInfo: JSON object containing structured data and metadata related to the action
- Open: Interactive button to view detailed information or navigate to related resources
Filtering Capabilities
The logs interface provides multiple filtering options to help you find specific activities:
Basic Filters
- User Filter: Search for logs by user email address with autocomplete functionality
- Action Filter: Filter by specific action types or keywords
Advanced Filters
Click "More Filters" to access additional filtering options:
- Details Filter: Search within action details and descriptions
- Date Range: Filter logs by creation date using a date picker with start and end dates
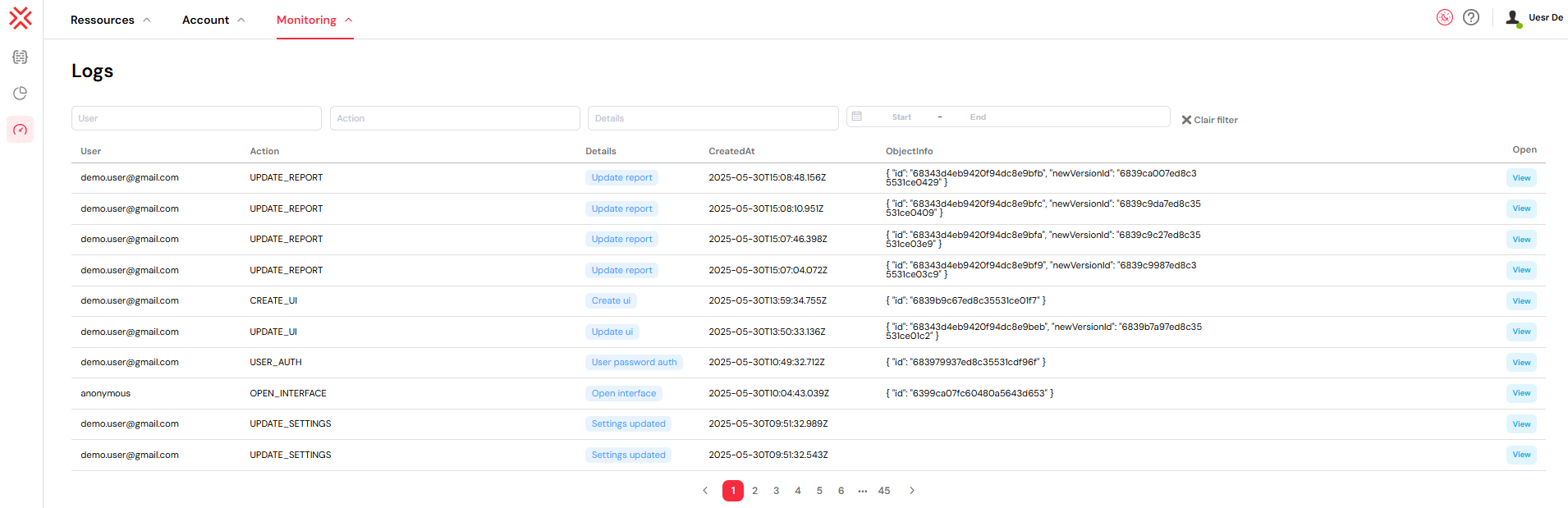
Filter Management
- Use the X button to clear all filters and return to the complete log view
- Filters are applied in real-time as you type or make selections
- Combine multiple filters for precise log searches
Interactive Features
View Action Details
Each log entry includes a "View" button that provides context-aware navigation:
- USER_AUTH: Opens the user profile page for authentication-related logs
- ADD_USERS_TO_GROUP / REMOVE_USERS_FROM_GROUP: Navigates to the specific role management page
- UPDATE_INSTANCE: Opens the relevant instance configuration page
- OPEN_INTERFACE: Directs to the specific web interface page
- PROCESS_EXECUTION: Links to process design or run monitoring
Pagination
- Navigate through large log datasets using the pagination controls
- Configurable items per page (default: 10 entries)
- Real-time page count updates based on filtered results
Common Use Cases
Security Auditing
Monitor security-related activities:
- Authentication Events: Track user login attempts and security events
- Permission Changes: Review role and permission changes
- Access Patterns: Monitor unusual access patterns and suspicious activities
- Configuration Changes: Track changes to platform settings and security configurations
System Debugging
Investigate system issues and performance:
- Process Execution: Trace process instances and workflow execution
- Interface Access: Track web interface usage and performance issues
- Integration Calls: Monitor external API calls and system integrations
- Database Operations: Track database interactions and performance issues
Compliance Reporting
Generate reports for regulatory and business requirements:
- User Activity Reports: Generate activity reports for specific users or time periods
- Change Documentation: Document system changes for regulatory requirements
- Audit Trails: Maintain comprehensive audit trails for data governance
- Access Reviews: Review access patterns for compliance audits
Log Categories and Actions
User Management Actions
Track user-related activities:
- USER_AUTH: User authentication and login events
- CREATE_USER: New user account creation
- UPDATE_USER: User profile modifications
- DELETE_USER: User account deletions
- BLOCK_USER / UNBLOCK_USER: User account status changes
Role and Permission Actions
Monitor access control changes:
- ADD_USERS_TO_GROUP: User assignments to roles or groups
- REMOVE_USERS_FROM_GROUP: User removals from roles or groups
- CREATE_ROLE: New role creation
- UPDATE_ROLE: Role modifications
- DELETE_ROLE: Role deletions
Process and Instance Actions
Track workflow execution and management:
- START_PROCESS: Process instance initiation
- UPDATE_INSTANCE: Process instance modifications
- END_INSTANCE: Process completion or termination
- VALIDATE_TASK: Task completion and validation
- UPDATE_TASK: Task modifications
System Configuration Actions
Monitor platform configuration changes:
- UPDATE_SETTINGS: Platform settings modifications
- UPDATE_MAIL_PROVIDER: Mail provider configuration changes
- UPDATE_AUTH_SETTINGS: Authentication system changes
Tips for Effective Log Management
Search Strategies
Optimize your log searches:
- Use Date Filters: Narrow down searches to specific time periods for faster results
- Combine Filters: Use multiple filter criteria to find exact log entries
- Action-Specific Searches: Use action filters to focus on specific types of operations
- User-Focused Analysis: Filter by specific users to track individual activity patterns
Regular Monitoring
Establish monitoring routines:
- Daily Reviews: Check logs regularly for unusual activity patterns
- Weekly Summaries: Generate weekly activity summaries for trend analysis
- Monthly Audits: Perform monthly comprehensive audits for compliance
- Alert Integration: Use with instances monitoring for automated alerting
Performance Considerations
Optimize log management for large datasets:
- Date Range Limits: Use appropriate date ranges to limit result sets
- Specific Filters: Apply specific filters before broad searches
- Export Capabilities: Export filtered results for offline analysis
- Archive Strategy: Implement log archiving for long-term retention
Navigation Path: Monitoring → Logs
Log Integration & Analysis
Development Integration
Logs provide insights for development activities:
- Project Setup: Track project creation and configuration changes
- Web Interface Design: Monitor interface usage and identify popular features
- Process Design: Analyze process execution patterns and optimization opportunities
- Database Integration: Track database operations and performance issues
- Integration: Monitor external API calls and integration health
- Test & Deploy: Track deployment activities and environment changes
Administration Integration
Logs support comprehensive platform administration:
- User Management: Track user account changes and access patterns
- Role Management: Monitor role assignments and permission changes
- Authentication: Track login attempts and security events
- Settings: Monitor platform configuration changes
- Mail Management: Track email operations and delivery issues
- Instances Monitoring: Correlate log data with monitoring metrics
- Run Management: Deep dive into process execution details
Compliance & Security
Use logs for security and compliance requirements:
- Regulatory Compliance: Meet audit requirements with comprehensive activity tracking
- Security Monitoring: Identify potential security threats and unusual access patterns
- Change Management: Document all system changes for governance purposes
- Access Reviews: Regular review of user access and activity patterns
Next Steps
Continue building your monitoring and security infrastructure:
Enhanced Monitoring:
- Instances Monitoring - Real-time monitoring with automated alerting
- Run & Instance Management - Detailed process instance management and control
- Settings - Configure logging preferences and retention policies
- Mail Management - Set up email notifications for critical log events
Security & Administration:
- User Management - Manage users based on activity patterns from logs
- Role Management - Adjust permissions based on access pattern analysis
- Authentication - Strengthen security based on authentication log analysis
- Home Redirection - Configure personalized experiences based on usage patterns
Development Optimization:
- Project Setup - Optimize project configurations based on usage data
- Web Interface Design - Improve interfaces based on usage analytics
- Process Design - Optimize processes based on execution patterns
- Monitor & Run - Implement comprehensive runtime monitoring