Authentification & SSO
1. Authentication
One of the essential features of SoftyFlow is to determine the authentication method used for users accessing the platform and defining a password policy.
To access the Authentification & SSO inteface, click a menu from the left top pane, then you can find it by navigating to the "AUTH" tab, located in the top lmenu bar, or simply navigate to the path /ide/auth within the IDE.
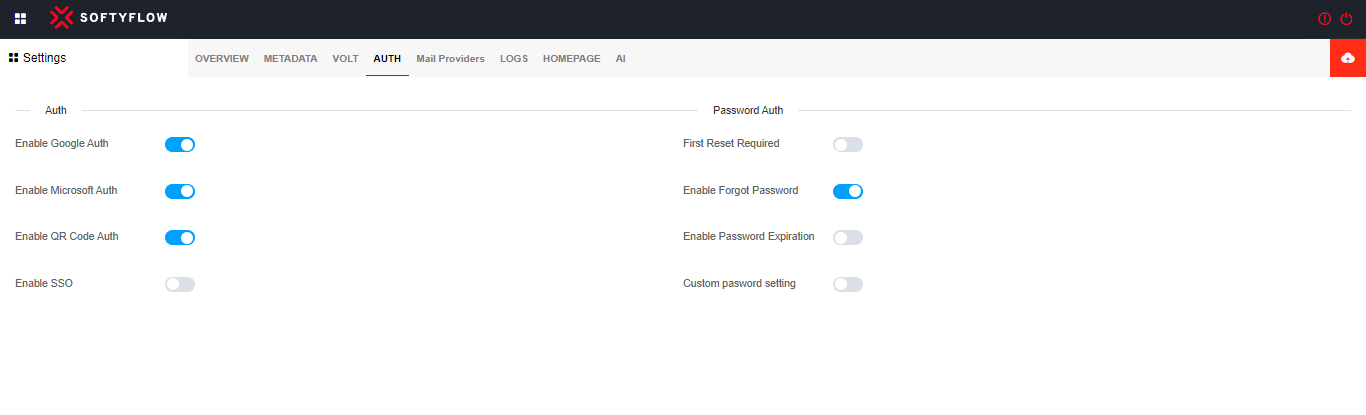
2. Different authentication methods
Google Auth : Google Authenticator is a two-factor authentication (2FA) application developed by Google to enhance the security of user accounts by adding a second verification step during login.
Microsoft Auth : Microsoft Authenticator, is a popular two-factor authentication (2FA) application developed by Microsoft. Similar to Google Auth, it adds an extra layer of security to user accounts by requiring a second verification step during the login process.
QR Code Auth : QR code authentication, is a method of authentication that utilizes Quick Response (QR) codes to verify a user's identity. It involves scanning a unique QR code presented by a service or website using a mobile device or a dedicated QR code reader.
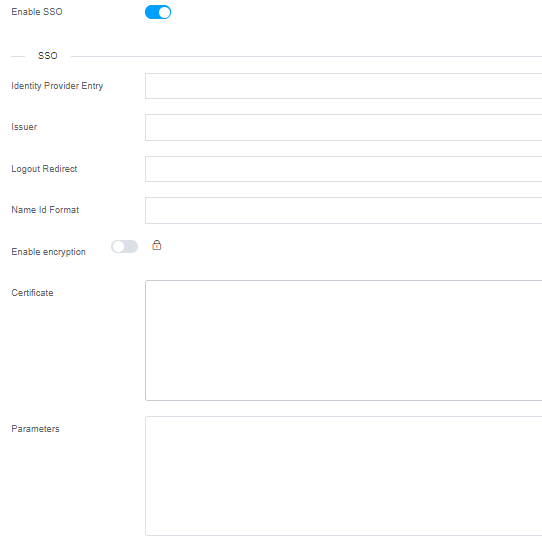
SSO : It is an authentication mechanism that allows users to access multiple applications or systems with a single set of login credentials.
To configure SSO, you need to provide the following details:
Identity Provider Entry: This is the system or service that handles authentication and provides user credentials. The IDP is responsible for authenticating the user and verifying their identity.
Issuer: The issuer generates security tokens, such as JSON Web Tokens (JWTs) or Security Assertion Markup Language (SAML) assertions. These tokens contain claims or assertions about the user, including their identity, roles, permissions, and other relevant attributes.
Logout Redirect: Logout Redirect is a mechanism in SSO that determines where a user should be redirected after they have successfully logged out from a service or application. It ensures that users are redirected to the appropriate destination, such as a logout confirmation page or the login page of the identity provider.
Name Id Format: Name ID Format is a standard used in SSO protocols like SAML to define the format in which the unique identifier of the user (Name ID) is communicated. It specifies how the identity provider represents and formats the user's identifier, such as an email address, transient identifier, persistent identifier, or other formats.
Enable encryption: Enable Encryption refers to a configuration option in SSO that allows the encryption of sensitive data exchanged between the identity provider and the service provider. Encryption ensures that the data transmitted, such as user attributes, tokens, or authentication assertions, remains confidential and secure during transit.
Certificate: In SSO, certificates are cryptographic files used to establish trust and secure communication between the identity provider and the service provider. Certificates contain public keys used for encryption and digital signatures. The identity provider signs tokens or assertions with its private key, and the service provider can verify the authenticity of these tokens using the identity provider's public key.
Parameters: In the context of SSO, parameters refer to the values or variables that are included in the SSO request or response messages. These parameters convey specific information required for authentication and authorization. Examples of parameters include the Assertion Consumer Service (ACS) URL, RelayState, RequestedAuthnContext, and various other parameters defined by the SSO protocol being used.
3. Password
First Reset Required : SoftyFlow has implemented this feature to enable users to modify their password during the initial login session.
Enable Forgot Password : SoftyFlow used this feature to help users recover their password if they forget it.
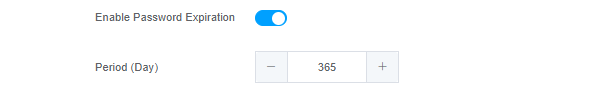
Enable Password Expiration : This mechanism enforces scheduled password modifications for users, with the duration of each period being determined by the system administrator.
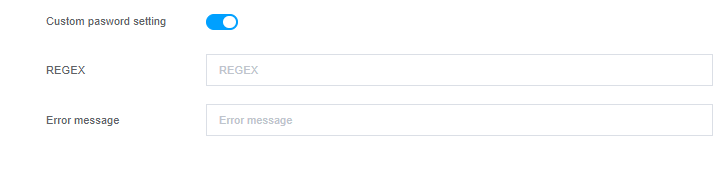
Custom password setting : This functionality pertains to the capacity to establish explicit prerequisites and limitations for user passwords through the utilization of a regular expression. Furthermore, it is possible to configure an error message to be displayed in the event that the regular expression is not respected.